Experts in transport cybersecurity, from EV charging, to digital key management
Who do we serve?
We help the transport industry to protect its revenue, create new offerings and fight cybercrime
Providing transport ecosystem cybersecurity
Explore each of our transport cybersecurity solutions

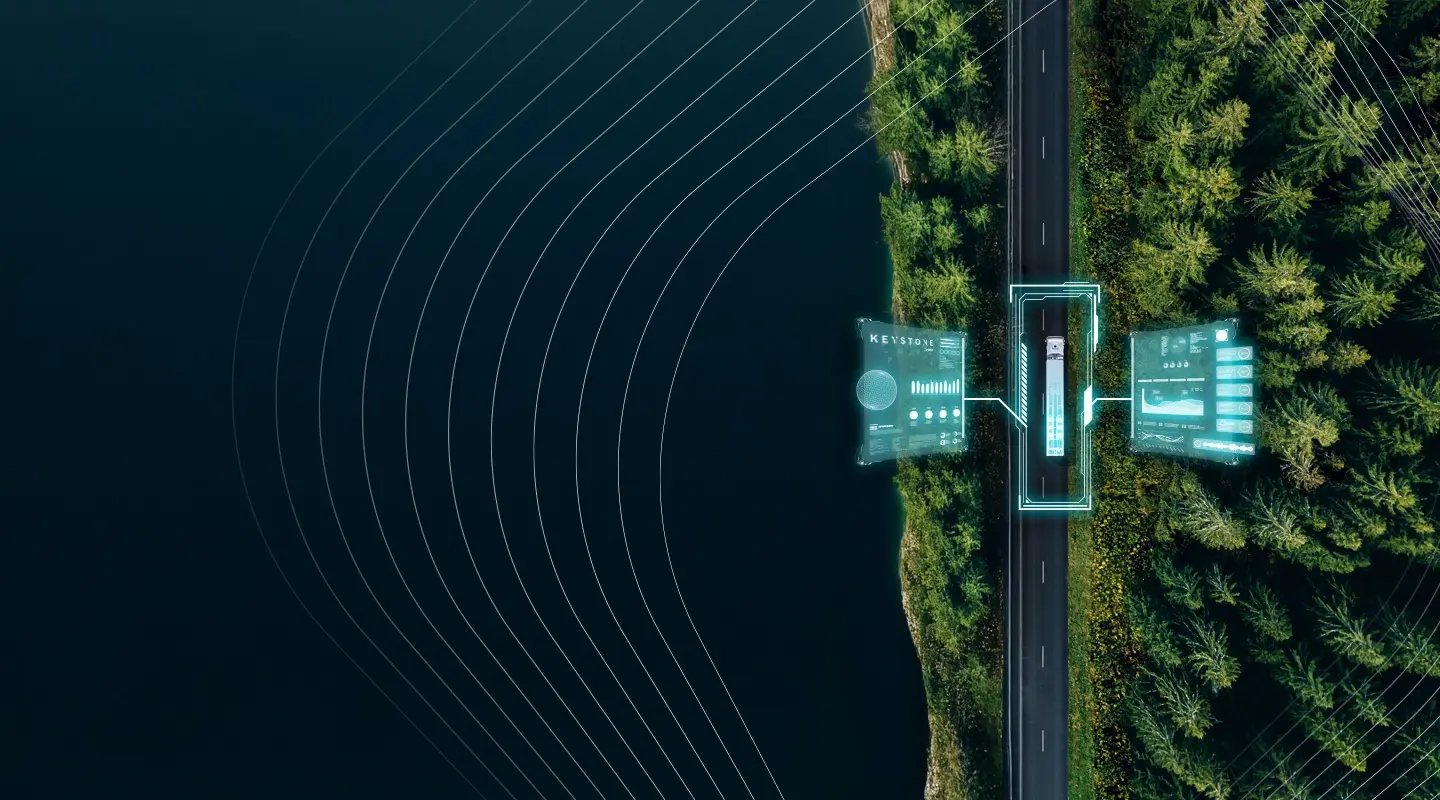
Keystone
Keystone by Irdeto is a secure, permission-based vehicle digital key solution that leverages Bluetooth™ Low Energy technology to enable proximity-based vehicle access using a smartphone. Additionally, Keystone by Irdeto supports Trailer Validation, an industry-first solution that mitigates costly mis-pulls and ensures the right asset is attached from the yard every time!

CrossCharge
Irdeto CrossCharge is a cutting-edge modular product line designed to cater to the diverse needs of the EV charging ecosystem. Whether you’re a CPO, MSP or an OEM, Irdeto CrossCharge delivers cryptographic keys and certificates ensuring secure and seamless EV charging experiences, including V2G Root, as the foundational trust layer for EV Charging.

Keys & Credentials for transportation
Irdeto Keys & Credentials is a managed security service for the complete lifecycle of trusted identities, secrets and secured firmware for connected embedded products. It simplifies the design and manufacturing of secure devices, by easily integrating into silicon and at the production lines.




Latest insights in our knowledge base
We love sharing our knowledge and expertise. Below are some recent examples






/Images/Module%20-%20footer/spiral.svg)
