Astro and Irdeto redefine the streaming experience

Protect your content, brand and investments against pirates
Comprehensive protection
- End-to-end security coverage
- Safeguards content, brand and investments
- Ensures compliance with content requirements
- Helps mitigate piracy losses effectively

Agile detection and enforcement
- Proactive piracy detection
- Swift analysis of infringement instances
- Disrupts payment processes for pirates
- Targeted enforcement and takedown actions

Integrated technology and human intelligence
- Advanced forensic watermarking technology
- Continuous proactive monitoring
- Localized investigative services
- Collaborative global partnerships for enforcement

Winner of “2024 Best Anti-Piracy Solution”
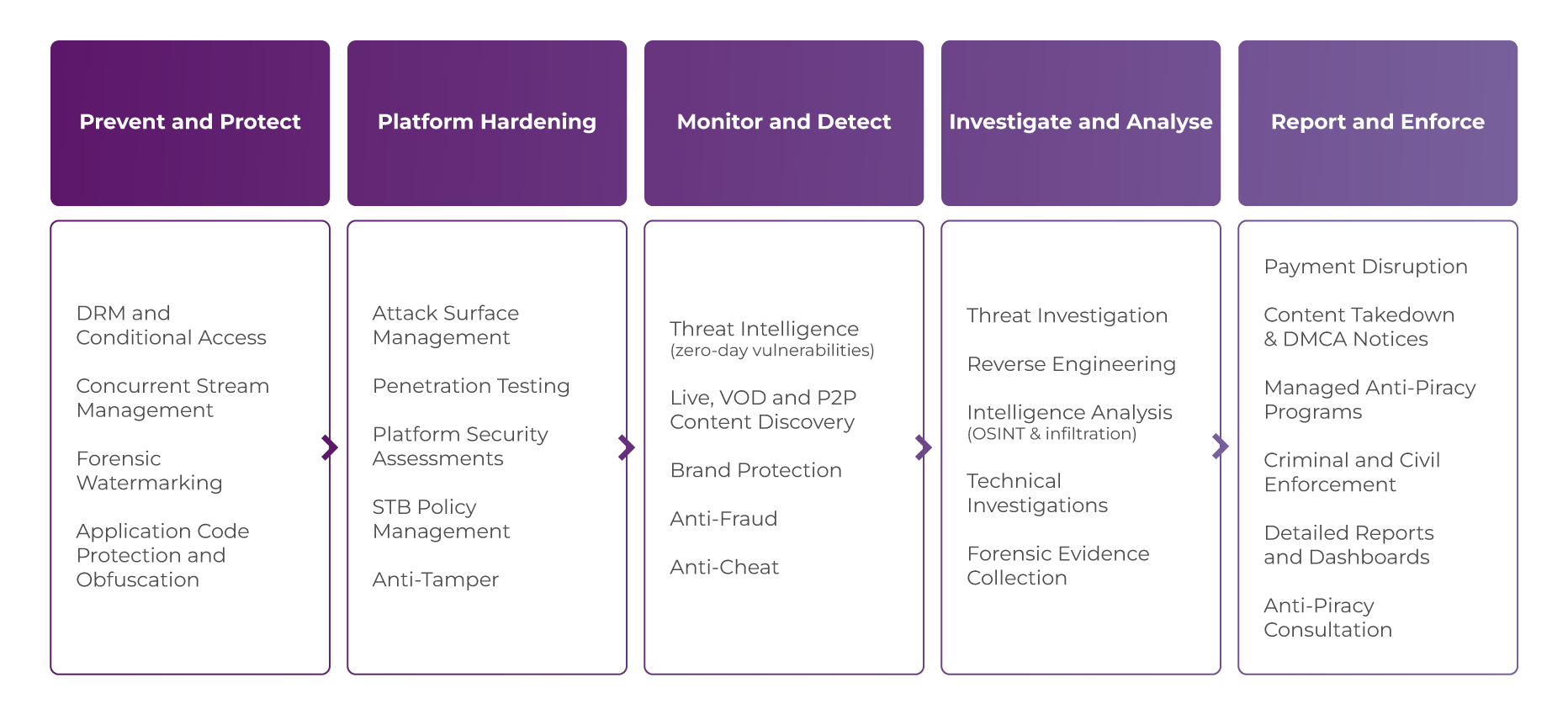
Our 5-step program for E2E anti-piracy and cybersecurity management
Protecting sports revenue, preserving the passion
Case study: Explore success stories where premium video providers, with Irdeto’s expertise, fought piracy and secured content, revenue and fan engagement, keeping sports thriving worldwide.

















/Images/Module%20-%20footer/spiral.svg)
