
Astro and Irdeto redefine the streaming experience

End-to-end solutions and expertise for streaming, broadcast and hybrid video portfolios
Elevating video entertainment together
Studios and sports rights holders
Safeguard premium content from piracy and unauthorized distribution, ensuring maximum revenue and viewer engagement.

Broadcasters and streaming services
Deliver high-quality, secure streaming experiences to millions of viewers across multiple platforms.

Pay-TV and telecommunications companies
Enhance service offerings and protect revenue streams with advanced video security solutions.

Video entertainment solutions
Discover our video entertainment solutions suite

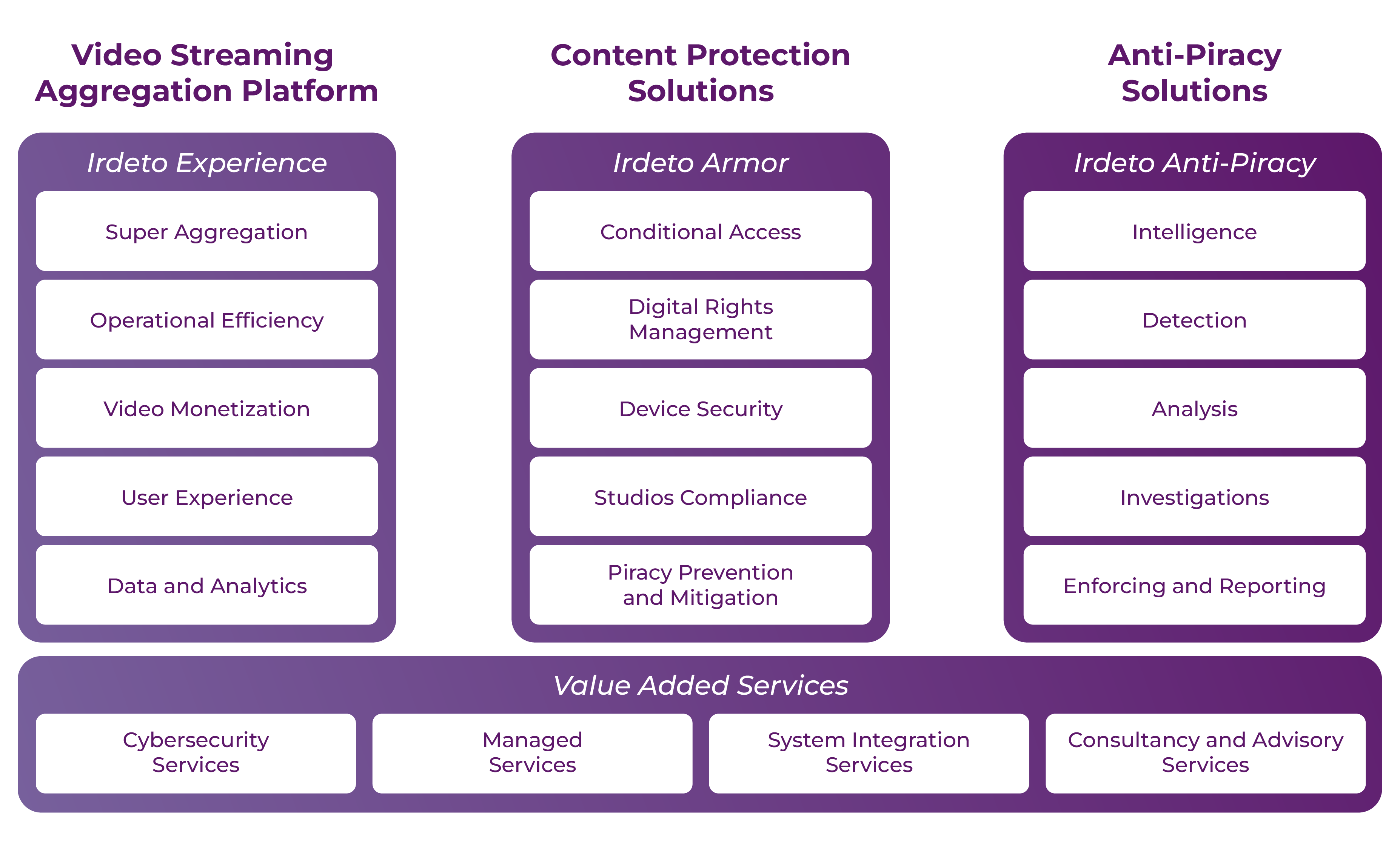
Video streaming aggregation platform
A unified platform that empowers operators with a seamless, end-to-end solution for OTT, broadcast TV, and hybrid services. Designed for scale and flexibility, it aggregates content, insights, services, and monetization tools within a tailored deployment model.

Irdeto Armor
Providing comprehensive content protection solutions, Irdeto Armor safeguards digital assets from unauthorized access and piracy across broadcast, streaming and hybrid platforms.

Irdeto Anti-Piracy
Offering comprehensive end-to-end solutions for cybersecurity and piracy management, our solution protects content, brands and investments with proactive detection, enforcement actions and advanced forensic watermarking technology.

Irdeto Managed Services
Part of Irdeto Video Entertainment added value services, Irdeto Managed Services enables operators to focus on core activities and deliver exceptional viewing experiences to customers by optimizing content delivery, enhancing security and reducing operational costs.

Keys & Credentials for routers
Providing secure, vendor-neutral lifecycle management for routers, gateways and Wi-Fi extenders, safeguarding ISPs and broadband networks from cyber threats.

Our video entertainment solutions portfolio
Scaling businesses, enhancing user experiences and maximizing monetization



How we work with partners
Learn more on how we support each other through trusted collaboration – our brochures highlight joint efforts, shared success and the value created through working together.

The Synergy of Ateme & Irdeto in High-Quality and Secure Streaming



Irdeto Metadata Aggregation and Enrichment with Simply.TV

Driving engagement and loyalty across OTT, pay-TV, and broadcast with Advanced Content Discovery

Securing Live Sports Content

Securing VOD Content in a High-Stakes Digital World
Corporate Star Awards 2024 – Best Employee Engagement Program
NAB Awards 2024 – Leadership in Sustainability
Latest insights in our knowledge base
Explore our knowledge base for more






/Images/Module%20-%20footer/spiral.svg)
