Astro’s transformation with sooka
Powered by Irdeto Experience to lead in streaming
Download case study
Complete coverage against video piracy
Comprehensive protection
- Ensure end-to-end security across your services
- Protect your content, brand and investments
- Reduce revenue loss from piracy
- Stay compliant with content licensing requirements
- Build and maintain viewer trust
Agile detection and enforcement
- Execute proactive detection of piracy threats
- Get swift analysis of infringement instances
- Disrupt payment channels used by pirates
- Take targeted enforcement and takedown actions
- Respond fast to shut down piracy

Integrated technology and human intelligence
- Track misuse with forensic watermarking
- Detect threats through proactive monitoring
- Address issues with local investigators
- Enforce rights via global partnerships
- Strengthen protection with tech and experts

Real-world successes from our anti-piracy efforts
71%
decrease in pirated IPTV and credential ads
25%
reduction in CDN costs caused by piracy and abuse
93%
drop in pirate site traffic via payment disruption
Leading the way in anti-piracy solutions
Intelligence
Data-driven insights for proactive security measures.
Detection
Early identification of piracy threats with advanced technology.
Analysis
In-depth scrutiny to assess piracy risks and impacts.
Investigations
Expert-led inquiries into piracy incidents for swift resolutions.
Enforcement and reporting
Effective enforcement actions and comprehensive reporting mechanisms.
End-to-end content security
Unmatched 360° coverage that safeguards revenues by disrupting piracy effectively.
Protecting sports revenue, preserving the passion
Explore success stories where premium video providers, with Irdeto’s expertise, fought piracy and secured content, revenue and fan engagement, keeping sports thriving worldwide.

Winner of “2024 Best Anti-Piracy Solution”
Our 5-step program for E2E anti-piracy and cybersecurity management
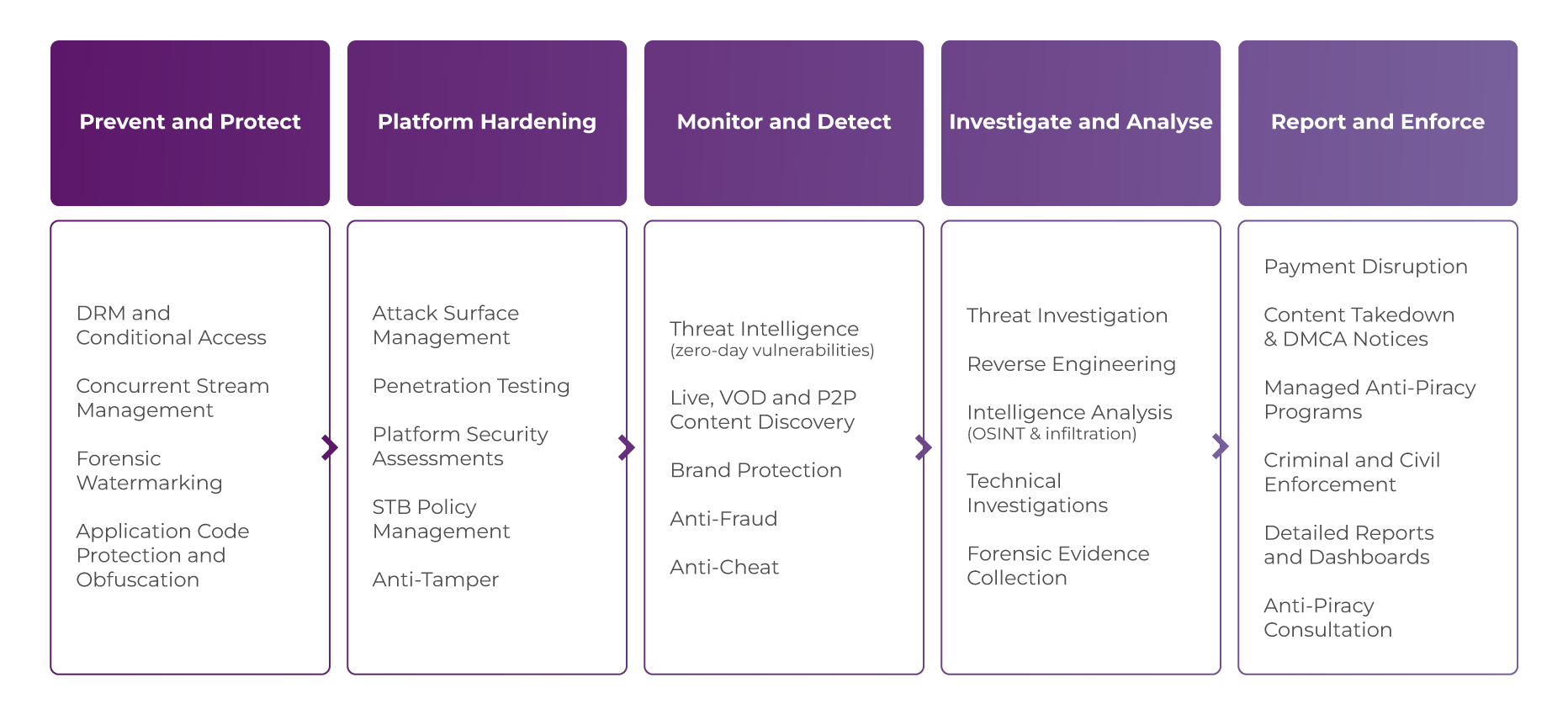
Anti-piracy solutions portfolio






Brand protection
- Copyright and trademark infringement detection
Cyber services
- Threat intelligence
- Investigations and enforcement services
- Penetration testing
- Platform security assessment
- Consulting
Online piracy detection
Coverage
- P2P
- Live (sports, events, PPV)
- Web VOD
- Apps (detection and enforcement)
Services
- Monitoring
- Analysis
- Verification
- Takedowns
Payments disruption
- Investigations
- Reporting
- Prevention
Site blocking support
- Monitoring
- Block verification
Watermarking
- TraceMarkTM for distribution
- TraceMarkTM for OTT
- TraceMarkTM for broadcast
Latest insights in our knowledge base
Explore our knowledge base for more

Video Entertainment
January 9, 2026
Extending trust into live video with C2PA

Video Entertainment
August 5, 2025
Tackling football piracy: How to protect the..

Video Entertainment
June 25, 2025
Monetization for broadcasters: Beyond..

Video Entertainment
May 8, 2025
How C2PA is bringing authenticity back to the..

Video Entertainment
September 10, 2024
Irdeto leverages IMDb data to help to combat..

Video Entertainment
July 31, 2024
Can we win the battle against live sports piracy?
Let’s stop piracy together
Something went wrong when submitting the form, please refresh and try again.
/Images/Module%20-%20footer/spiral.svg)
